MACHINE LEARNING DRIVEN NETWORK TRAFFIC ANALYSIS FOR CYBERSECURITY: A COMPARATIVE STUDY OF SUPERVISED AND UNSUPERVISED LEARNING APPROACHES
Keywords:
Machine Learning, , Network Traffic Analysis, Anomaly Detection, Supervised Learning, Unsupervised LearningAbstract
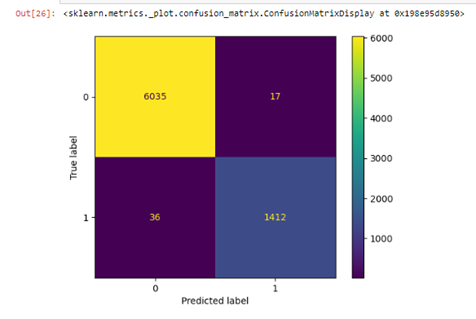
This study looks at how well machine learning (ML) methods work in cybersecurity, focusing on their ability to tell apart malicious and normal network traffic. Using the CICIDS2017 dataset, we compare supervised learning models like Random Forest and Support Vector Machines with unsupervised techniques such as K-means clustering and Isolation Forest. We evaluate their performance using multiple metrics, including accuracy, precision, recall, F1-score, and cluster validity indices, to find the most effective approach for spotting anomalies in network data. The results show that Random Forest delivers the best overall performance, achieving over 99.4% accuracy with very few false negatives. Meanwhile, unsupervised methods excel at detecting new, previously unseen patterns without needing labeled data. In particular, the Isolation Forest model achieves a recall of 93%, making it highly effective at identifying anomalies. K-means clustering also performs well, clearly separating traffic patterns with strong Silhouette scores (0.8622) and favorable Davies-Bouldin indices (0.6063).
Published
How to Cite
Issue
Section
Copyright (c) 2025 Abdulrahman Tunde Alabelewe, Nasir Shinkafi, Samson Adeyinka, Suleiman Abu Usman, Maryam Safiyanu Masari, Muhammad Auwal Bello, Joshua Yakubu Anche

This work is licensed under a Creative Commons Attribution 4.0 International License.
How to Cite
Most read articles by the same author(s)
- Godwin A. Otu, Oludele Awodele, Sola A. Adeniji, Henry O. Mafua, Kehinde A. Olayanju, Adeniyi U. Adedayo, Suleiman A. Usman, Samson Adeyinka, Aisha Ramalan, Maryam Masari, PREDICTION ACCURACY ANALYSIS OF MACHINE LEARNING CLASSIFIERS ON STUDENT COURSE ASSESSMENT METHODS , FUDMA JOURNAL OF SCIENCES: Vol. 8 No. 6 (2024): FUDMA Journal of Sciences - Vol. 8 No. 6 (Special Issue)




